Do You Know OSI?
A dive into the seven-layer Open Systems Interconnection (OSI) model.

A daily selection of features, industry news, and analysis for AV/IT professionals. Sign up below.
You are now subscribed
Your newsletter sign-up was successful
The OSI model is a product of the Open Systems Interconnection project at the International Organization for Standardization (ISO), maintained by the identification ISO/IEC 7498-1.
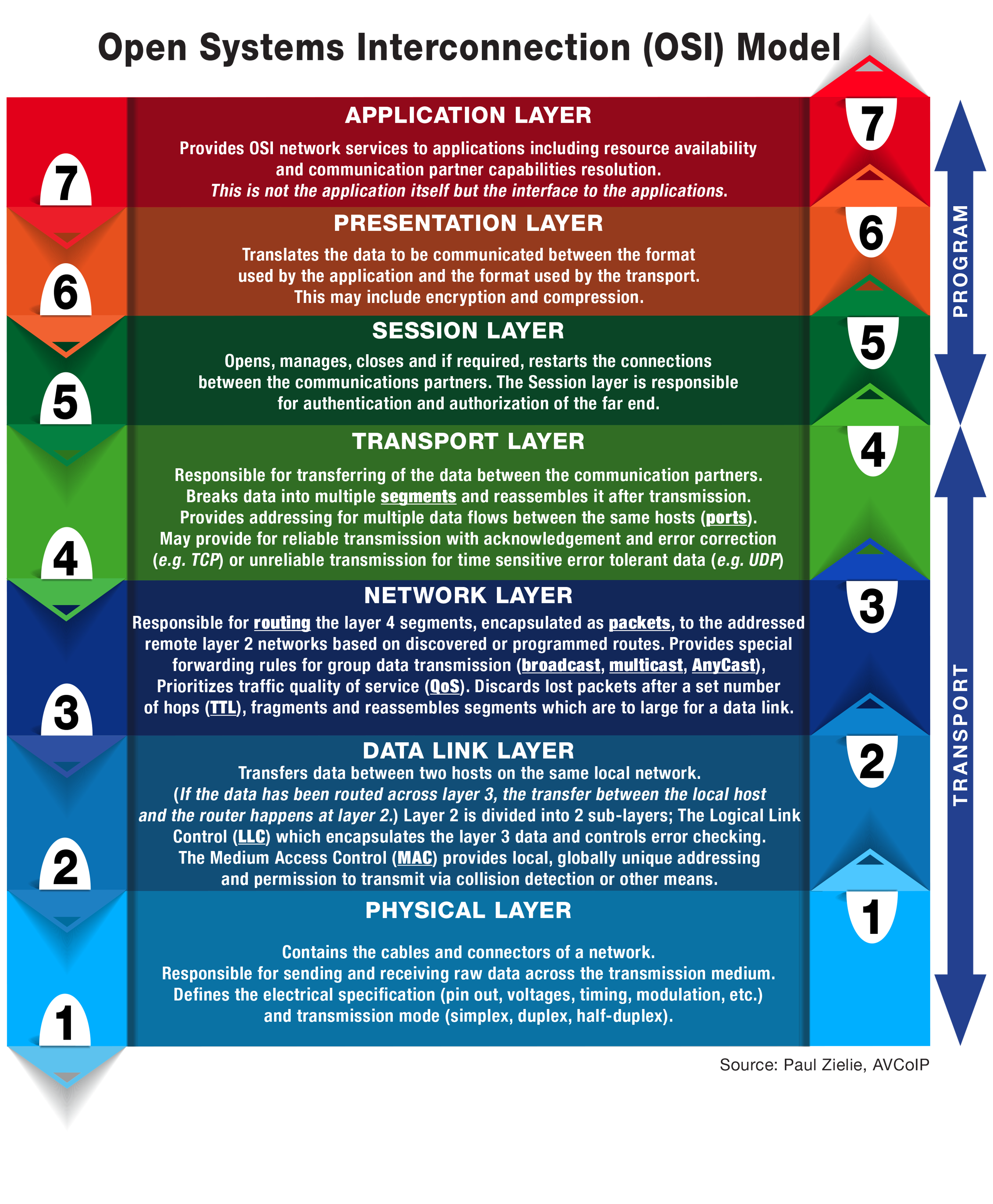
Consulting Solutions Architect at AVCoIP LLC, Paul Zielie provides the following snapshot:
Layer 7: Application Layer Provides OSI network services to applications including resource availability and communication partner capabilities resolution. This is not the application itself but the interface to the applications.
Layer 6: Presentation Layer Translates the data to be communicated between the format used by the application and the format used by the transport. This may include encryption and compression.
Layer 5: Session Layer Opens, manages, closes and if required, restarts the connections between the communications partners. The Session layer is responsible for authentication and authorization of the far end.
Layer 4: Transport Layer Responsible for transferring of the data between the communication partners. Breaks data into multiple segments and reassembles it after transmission. Provides addressing for multiple data flows between the same hosts (ports). May provide for reliable transmission with acknowledgement and error correction (e.g. TCP) or unreliable transmission for time sensitive error tolerant data (e.g. UDP)
Layer 3: Network Layer Responsible for routing the layer 4 segments, encapsulated as packets, to the addressed remote layer 2 networks based on discovered or programmed routes. Provides special forwarding rules for group data transmission (broadcast, multicast, AnyCast), Prioritizes traffic quality of service (QoS). Discards lost packets after a set number of hops (TTL), fragments and reassembles segments which are too large for a data link.
A daily selection of features, industry news, and analysis for tech managers. Sign up below.
Layer 2: Data Link Layer Transfers data between two hosts on the same local network. (If the data has been routed across layer 3, the transfer between the local host and the router happens at layer 2.) Layer 2 is divided into 2 sub-layers; The Logical Link Control (LLC) which encapsulates the layer 3 data and controls error checking. The Medium Access Control (MAC) provides local, globally unique addressing and permission to transmit via collision detection or other means.
Layer 1: Physical Layer Contains the cables and connectors of a network. Responsible for sending and receiving raw data across the transmission medium. Defines the electrical specification (pin out, voltages, timing, modulation, etc.) and transmission mode (simplex, duplex, half-duplex).
Layer 4 Dive
TCP is called reliable because it can retransmit lost packets. UDP does not have the capability to do that.
AV Technology contributor, Phil Hippensteel provided the following: The transport layer has two protocols, TCP and UDP. In the theory of the seven-layer OSI model, Layer 4 (L4) is responsible for segmentation and delivery between the end points. That is, it isn’t concerned with what happens to a segment (message) as it passes between two switches or two routers. It is concerned with how it is initially sent and how it is finally received. As most of us have learned by now, TCP is called reliable because it can retransmit lost packets. UDP does not have the capability to do that because it does not contain a sequence number to allow the receiver to determine if a packet was dropped. However, there is more to TCP than retransmissions. TCP can exercise flow control to adjust to the available bandwidth between the end stations. It can also detect a state of congestion in the network and slow its transmission or even completely stop transmitting. It does this by detecting that the network is beginning to drop segments.
Research has demonstrated that the current method of detecting congestion isn’t working well for TCP. It’s true that it detects congestion and retransmits lost segments. But, it also adds significant delay to delivery of the segments. Additionally, its adjustment to congestion is slow. Often dozens or hundreds of packets are dropped, when only one would signal the congested situation.
As a result, major players on the IT side have introduced technologies to try to avoid TCP’s problems. A few, including TCP BBR, Google’s QUIC and the active queue management techniques proposed within the IETF (Internet Engineering Task Force). On the AV side, SRT (Secure Reliable Transport) is also a method of getting some of the benefits of TCP goals but by using UDP. I would advise AV professionals to research each of these, as it will be some time before we see who the winners and who the losers are. In the meantime, here’s a list of critical questions to ask each company proposing to use of the techniques.
• If I deploy this technology, what are the benefits?
• Will I need to modify my existing devices that contain traditional TCP/IP protocol stack (Windows, Apple, Linux, etc.)?
• Is this technique headed for industry standardization?
• Is there any license or fee associated with its use?
With each of these proposed techniques, how the video is managed on the network is dependent on how the protocol works. We know traditional TCP is in trouble. But which of the new proposals might be its replacement?
Layer 3 Dive
The big difference between Layer 2 vs Layer 3 has to do with addressing.
Layer 3 is network layer. OSI states that the network layer is responsible for packet-forwarding, including routing through intermediate routers. This is possible because it knows the address of neighboring network nodes, and it also manages quality of service (QoS), and recognizes and forwards local host domain messages to the Transport Layer (Layer 4).
To understand Layer 3, it helps to understand its differences. Scott Kalarchik, of QSC’s system group, explained that the big difference between Layer 2 vs Layer 3 has to do with addressing. Better yet, he said, think of it as local addressing vs long distance addressing.
"Layer 2 networks use what is called a MAC address (which stands for Media Access Control Address) to send data around a local area on a switch,” Kalarchik wrote. “The MAC address is a local, permanent, and unique name for the device—think of it as the floor and room number of your office. The switch represents the doors and hallways in your office area. Layer 3 networks use Internet Protocol (IP) Address to send information between larger networks using routers. This information represents you virtual address in the physical world, the same way your mailing address tells a mail carrier how to find you. Instead of using a street address, street name, city, state, and zip code, the IP Address uses these four sets of numbers to narrow down your location in the virtual world. The Router represents you mail carrier as they handle the physical transport of the information."
An example: AES67 is a Layer 3 protocol suite based on existing standards and designed to enable interoperability among various IP-based audio networking standards, such as Ravenna, Livewire, Q-LAN, and Dante. Because Dante uses the Internet Protocol to manage the way audio is moved around the network, it is referred to as a layer 3 solution.
Layer 2 Dive
Layer 2 is particularly important in the delivery of audio and is used in every implementation of TCP/IP.
Phil Hippensteel provided the following: The data link level, is one which is particularly important in the delivery of audio and is used in every implementation of TCP/IP.
Layer 2 (L2), the data link level of the OSI model sits between the physical level and the network layer. The physical level is primarily responsible for signal creation and timing on the media of choice—wires, fibers, or wireless. The network layer in TCP/IP is where IP exists. Its most critical function is the proper use of IP addresses, which are nearly always created in software. The data link layer is responsible for access to the physical media, for arranging the bit stream into frames, for controlling flow between stations attached to the media, and detecting errors. Since the primary data link technology used in TCP/IP is Ethernet, we will emphasize its implementation. However, in wide area technologies and data centers, there are several other methods in use.
When the OSI model was conceived, its creators separated L2 into two parts. The upper part, responsible for sending and receiving messages to the IP level, was called logical link control (LLC). The lower level, responsible for sending and receiving the bit stream on the physical media, was called media access control (MAC). LLC was responsible for decisions about how the stream was to be formatted and how flow between the end stations was to be controlled. Additionally, it was to report if errors had occurred during transmission. However, in Ethernet, flow control is not used except in Wi-Fi. The MAC layer is different for wired Ethernet than for wireless Ethernet.
The MAC layer of wired Ethernet has not seen extensive variation as Ethernet has evolved from 10Mbps to 10Gbps. Frame synchronization is based on transmitting 56 alternating ones and zeros followed by the byte 10101011. Addressing has consistently been based on 48-bit physical addresses that we call the MAC addresses. In this way, the spanning tree protocol (STP) for bridges and switches can be implemented. STP automatically eliminates loops in the physical network and assures that there is only a single path between each pair of stations. Likewise, the MAC addresses allow for the implementation of shortest path bridging (SPB). SPB is the basis for mesh networks, which are widely used in computer centers and global spanning networks that want to avoid the issues of IP-level multicasting.
In either wired or wireless Ethernet, error detection is done with a method call CRC-32. A code of 32 bits is divided into the bit stream using binary arithmetic. The remainder, which is always 32 bits in length, is appended to the frame as an error check code. Finally, a level of quality of service (QOS) or service priority can be implemented within L2.
So, with functions such as flow control, error detection, and QOS implemented at L2, why would engineers not choose to do the same at L3, the IP layer? The most important reason is because these functions can be done in firmware rather than in software. In nearly all cases, this makes their implementation more efficient.
Layer 1 Dive
The robustness of Layer 1 infrastructure supporting IP traffic will play a substantial role in the quality of your AV signal performance.
Layer one often gets short shrift, but it’s the physical foundation that all others ride upon. Amy Hacker, commercial strategy manager supporting Panduit infrastructure and Atlona audiovisual solutions added the following.
The quality of the infrastructure directly correlates to the health and quality of the signals moving through a facility. The better the cable and connectivity, the less the customer needs to worry about pixel drops, fuzzy images, and other audiovisual artifacts that lessen the impact. This is especially critical as facilities transition to IP networks that are, by nature, more sensitive to moving high-bandwidth 4K/UHD/HDR video traffic over long distances—and often, sharing that same infrastructure with data traffic from other applications.
The presence of higher resolution 4K/UHD and HDR signals continues to proliferate in commercial AV environments as more content and compatible equipment come to market. The ability to manage the greater bit depth, color gamut and bandwidth requirements (among other performance parameters) that come with these formats goes far deeper than one might imagine.
The transition of AV components to IP for AV over IP transmission also creates a need to think through the AV strategy earlier in the planning process. AV systems have become part of the actual network deployment, which requires stronger communication with both the room or building architects and the consultants who design the local area network. The robustness of Layer 1 infrastructure supporting IP traffic will play a substantial role in the quality of your AV signal performance.

Cindy Davis is the brand and content director of AV Technology (AVT). She was a critical member of the AVT editorial team when the title won the “Best Media Brand” laurel in the 2018 SIIA Jesse H. Neal Awards. Davis moderates several monthly AV/IT roundtables and enjoys facilitating and engaging in deeper conversations about the complex topics shaping the ever-evolving AV/IT industry. She explores the ethos of collaboration, hybrid workplaces, experiential spaces, and artificial intelligence to share with readers. Previously, she developed the TechDecisions brand of content sites for EH Publishing, named one of the “10 Great Business Media Websites” by B2B Media Business magazine. For more than 25 years, Davis has developed and delivered multiplatform content for AV/IT B2B and consumer electronics B2C publications, associations, and companies. A lifelong New Englander, Davis makes time for coastal hikes with her husband, Gary, and their Vizsla rescue, Dixie, sailing on one of Gloucester’s great schooners and sampling local IPAs. Connect with her on LinkedIn.
