Byte-Sized Lesson: Security and TCP Handshakes
A daily selection of features, industry news, and analysis for AV/IT professionals. Sign up below.
You are now subscribed
Your newsletter sign-up was successful
This month, we shift our focus to an important security issue. We will combine some information about IP addresses, the TCP three-way handshake, and the role of the firewall. This security issue is important if you have an encoder, camera, or other device that periodically goes back to the manufacturer’s website to register its license or get updates. First, we require some background information.
There are two broad classes of IP addresses: public and private. Public addresses are intended for use outside private networks and are used in the public internet. Private addresses are to be used only on private enterprise networks such as those of schools, businesses, and hospitals. Addresses beginning with 192.168, 10, or 172.176 are nearly always private addresses. The firewall or residential gateway acting as a firewall, usually is placed between the public network (outside) and private network (inside). (We will interchange the terms “firewall” and “gateway” for this discussion.) One of the major roles of the firewall is to convert private addresses to public address and vice versa.
Related: Byte-Sized Lesson: Troubleshooting Connectivity
Two more facts are important. A TCP session is uniquely identified by four number patterns: the source IP address, the source port number, the destination IP address, and the destination port number. The client treats these four numbers as tags on the session and the server does the same thing. When the first packet in a session is sent from the client to the server, the firewall intercepts the flow and acts as a proxy. It will act as the end point of the session for the client by replacing the server’s IP address with its own address using a different port number. Then, it will forward the connection request to the server using the ISP’s public address that was assigned to the client’s location.
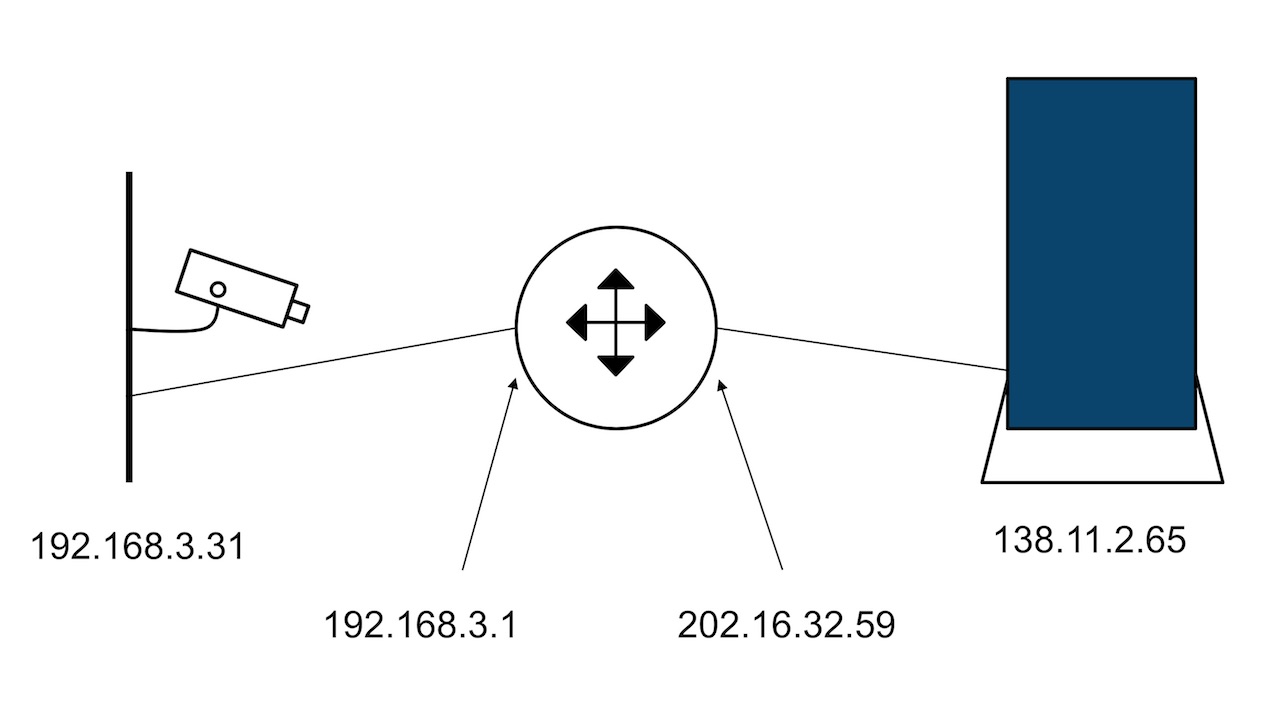
This may seem complicated. So, we’ll use this example (see the diagram above for reference). Your camera is assigned the address 192.168.3.31. The server is at 138.11.2.65. Your gateway is likely 192.168.3.1. Finally, your ISP assigned the address 202.16.32.59 to your gateway interface. Using the common notation (IP address: port number), the connection between the client and the gateway might be (192.168.3.31: 5050) to (192.168.3.1:5454) and then (202.16.32.59:4040) to (138.11.2.65:2090). Note that the internal connection uses only a private address. Likewise, the external connection uses only public addresses.
Now, consider the security implication of this procedure. The TCP handshake that establishes a connection is comprised of a three-way exchange of packets to negotiate the parameters to be used in the session. The first packet is simply a request by the client to open a session. The response from the server acknowledges the request and usually agrees with the set of parameters. The third packet, sent by the client, confirms the receipt of the second packet.
Now, it is practicable for the firewall to determine whether the initiator of the session is inside or outside. If the first packet is sent to a public address, the client is inside. If the first packet is sent to a private address, the client is outside. In the latter case, the session will be denied by directly dropping the packet. We don’t want sessions established by devices in the public internet.
A daily selection of features, industry news, and analysis for tech managers. Sign up below.
