
Quick Bio
Name: Kevin Gross
Title: Media Network Consultant
Company: AVA Networks
Professional network administrators are rightly concerned with the security of the networks they operate. The IT industry has developed design and operational practices to achieve the required level of security for networked systems. These practices are often intensive in terms of design and configuration effort and ongoing monitoring and maintenance. Working through security issues with the IT department has the potential to greatly complicate AV projects. IT involvement in AV projects is sometimes seen as increasing project effort and complexity with no functional benefit.
The Dream
What if we could avoid AV/IT interdependencies? Sure, networking is increasingly integral to AV systems, but why not just consider the networking to be part of the AV system? AV systems have always had communications and signal distribution components. Now, it just so happens that these functions are being accomplished using Cat-5 cable and some off-the-shelf communications gear built according to standards and protocols developed by the IT industry.
AV technology has been digital, networked, and computerized for some time now and AV contractors and designers definitely know their way around these technologies. Supplying the network for an AV system from the AV side assures that the network will meet the sometimes-demanding performance requirements of these systems. It eliminates finger pointing by ensuring that critical infrastructure for the AV system is under the control of the AV contractor and staff.
Security of AV systems is a concern for everyone. IT security measures clearly are designed to address this. As an efficient and simplified alternative, AV network security can be assured by an isolated network with access physically limited to those authorized to use and maintain it.
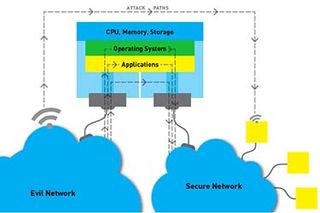
Huge evil networks contain villains that take attack paths terminating in damage to a secure network.Reality Check
A network used exclusively for AV is still a network and, as such, is subject to the same vulnerabilities as networks used for other applications. Expertise is required to assess and address these potential vulnerabilities. Many AV contractors do not have network security expertise, so they are likely not qualified to either secure a network or assess the security thereof.
We may be reluctant to admit it, but AV systems also use standard network technology because it enables useful connections with other systems in the installation and beyond. The isolated AV network may appear to meet our security requirements, but it may not fully meet operational requirements. In an increasingly interconnected world, users want or will soon want more than an isolated AV system can provide. Nevertheless, let’s have a closer look at the isolated AV network.
Air-gapped Networks
A simple way to assure the security of a network is to assure that it has no physical connections to potential attackers. This technique, known as air gapping, requires building a separate network infrastructure. Air-gapped networks are used in highly sensitive applications— think national security. In addition to being physically isolated, these networks also use common IT security measures, such as authentication and encryption. Building a true air-gapped network means no wireless networking, no direct or indirect connections to other networks, and securing physical access to all network and system components and cabling. Naturally, since most AV systems do not carry national secrets, and cost and convenience are important motivators, a dedicated AV network is not a true air-gapped network. Let’s look at some of the common vulnerabilities in these networks.
Multiple Network Connections
AV networks frequently contain control and monitoring appliances or computers. If there is a dedicated AV network, it is often desirable for the AV control system to interact with other systems and for the AV system to be monitored remotely or have the ability to automatically issue status notifications via text or email. Any AV system with a teleconferencing capability will have a telecommunications connection, sometimes through an analog POTS line, but increasingly through a network connection using VoIP techniques.
In assessing the security implications of devices with multiple connections, we optimistically assume the multiple connections to different networks are internally separated by a firewall. There are two problems with this assumption: first, it is typically based on how we hope these devices work, not on specifications or other information from manufacturers; and secondly, just like the firewall between you and the engine compartment in your car has holes for essential functions such as steering and electrical, firewalls in computers and appliances have intentional holes. Firewalls can also be breached entirely if the system is compromised by a software flaw or malware.
The Urge to Connect
The motivation to make additional connections to what is designed to be an isolated network is strong. Isolated networks may still be a desirable design practice for AV systems, but isolation should not be used as a substitute for good network security practices.

